Let's be blunt: ensuring HIPAA-compliant data transfer isn't what it used to be. The game has changed. It’s no longer just about checking the boxes on a traditional HIPAA audit. We're now operating in a far more complex legal environment where national security rules have fundamentally rewritten the playbook for healthcare organizations.
The core job—protecting Protected Health Information (PHI) as it moves from point A to point B—remains the same. But how you do it has become much more demanding.
The New Rules for HIPAA Compliant Data Transfer
For years, the focus was almost exclusively on the Health Insurance Portability and Accountability Act (HIPAA). Now, a critical layer of national security oversight sits on top of it. This means the old "checklist" approach to sending medical data is not just outdated—it's downright dangerous. Properly safeguarding PHI in transit today demands a sophisticated understanding of evolving legal frameworks, ironclad vendor agreements, and rigid data flow restrictions.
This isn't just some abstract legal theory. It has real, immediate consequences. Think about a research project transferring anonymized data to an international partner. A few years ago, that was a relatively low-risk activity. Today, that same transfer could trigger intense federal scrutiny and lead to catastrophic penalties if you get it wrong.
The Three Foundational Safeguards
Before we get into the new complexities, it’s crucial to have a rock-solid foundation. HIPAA compliance for data transfer is built on three pillars. These aren't suggestions; they are non-negotiable requirements that form the bedrock of any sound strategy.
Here's a quick breakdown of what they mean in the context of moving sensitive health information.
| Core Pillars of HIPAA Compliant Data Transfer |
| :— | :— | :— |
| Safeguard Type | Key Requirement | Example in Data Transfer |
| Technical Safeguards | Technology-based controls to protect PHI. | Using end-to-end encryption (like AES-256) for all data in transit and at rest, and enforcing strict user authentication to access the transfer platform. |
| Administrative Safeguards | Policies and procedures governing human behavior. | Conducting regular risk assessments of your transfer workflows, training staff on secure data handling, and having clear policies on who can send what, and to whom. |
| Physical Safeguards | Physical protection of IT systems and facilities. | Securing the servers that process data transfers in a locked, access-controlled data center, and implementing secure workstation policies for any device used to initiate a transfer. |
These three safeguards work together. Strong encryption is useless if an untrained employee accidentally sends PHI to the wrong person, which is why a holistic approach is the only one that works.
National Security Overlays on HIPAA
Here’s where things get really serious. A major change took effect in May 2025, when new U.S. federal rules began restricting the cross-border flow of sensitive health data—and this includes anonymized and de-identified information.
Under the International Emergency Economic Powers Act (IEEPA), you are now required to include specific language in your contracts. This language must explicitly prohibit foreign partners from reselling or transferring bulk U.S. health data to certain countries.
This isn't a minor regulatory tweak. The penalties for non-compliance are severe, reaching up to $368,136 per violation. Criminal penalties can be even worse, with up to 20 years in prison and $1 million in fines.
This shift means you can no longer view HIPAA in a vacuum. A data transfer that seems perfectly fine under HIPAA’s privacy rules could now be completely illegal under these new national security directives.
This new reality requires a much broader view of compliance. To stay out of trouble, it helps to understand proven data security compliance strategies that form the basis of any strong security program.
From now on, every Business Associate Agreement (BAA) and data transfer protocol must be re-evaluated through this dual lens of healthcare privacy and national security. The Department of Justice has even published sample contract language, which is a clear signal that they expect organizations to update their agreements immediately. Ignoring this evolution isn't just a compliance gap; it's a massive legal and financial gamble.
Building Your Technical Defense for Data Transfer

Alright, let's move past the legal paperwork and get into the real nuts and bolts of protecting PHI. Your technical defense is where the rubber meets the road—it’s the combination of software, protocols, and system architecture that actually keeps patient data safe during a transfer.
Honestly, even the most buttoned-up policies are worthless if your tech stack is leaky. This is one area you absolutely cannot afford to cut corners on.
It all begins with one foundational idea: encryption. Think of it like this: you wouldn't send cash through the mail in a clear envelope. You’d put it in a security envelope. Encryption does the same for your data, scrambling it into unreadable code so that even if it's intercepted, it's completely useless to a thief.
The Cornerstone of Encryption
When we're talking about HIPAA compliant data transfer, encryption isn't just a good idea; it's a non-negotiable. The HIPAA Security Rule is explicit, requiring technical safeguards that render PHI "unusable, unreadable, or indecipherable to unauthorized individuals."
This protection needs to cover data in two states:
- Data in Transit: This is your data on the move—like when an MRI scan is uploaded to a cloud server. Protocols like TLS (Transport Layer Security) or SSH (Secure Shell) create a secure, encrypted tunnel to protect it along its journey.
- Data at Rest: This is any PHI sitting on a server, a hard drive, or in the cloud, even if it's just for a moment. If that server gets breached, at-rest encryption ensures the files are nothing but gibberish without the right decryption key. For this, AES 256-bit encryption is the gold standard.
One of the most common mistakes I see is teams obsessing over transit security while forgetting about data at rest. A truly secure system locks down PHI at every single stage—from the second it leaves the source until it's securely wiped.
Choosing the Right Transfer Method
Let’s be clear: using your standard Outlook email or a personal Dropbox account to send PHI is asking for a data breach. You need tools built for the job—methods that are secure, reliable, and auditable. To build a strong technical defense, it is essential to implement secure HIPAA compliant document sharing practices.
Here are a few workhorse options I’ve seen used effectively:
| Transfer Method | Best Use Case | Key Consideration |
|---|---|---|
| Secure File Transfer Protocol (SFTP) | Automated, large-scale batch transfers—think nightly billing data or regular backups. | Your server must be hardened for HIPAA. This means rock-solid access controls, detailed logs, and a signed Business Associate Agreement (BAA). |
| Secure Cloud Services | On-demand file sharing, like a specialist needing to review a patient's CT scan from another clinic. | The provider must sign a BAA. Look for features like granular access permissions and comprehensive audit trails. Don't settle for less. |
| HTTPS-Based APIs | Integrating data transfer directly into your apps, like an EHR sending results to a patient portal. | The API needs robust authentication and must enforce encryption. Your developers have to get the implementation right and log every transaction. |
The right tool really depends on your specific workflow. A research facility swapping massive datasets will probably lean on SFTP, while a telehealth app is going to live and breathe with APIs and secure cloud storage.
The Power of Audit Trails and a Zero-Trust Mindset
In the world of HIPAA, if you can't prove it, you didn't do it. This is why audit trails (or access logs) are so incredibly important. A proper log doesn't just say a file was moved; it gives you a complete, unchangeable story of the event.
Your system should be logging:
- Who touched the data (user ID).
- What specific data was accessed (file name, patient record).
- When it happened (timestamp).
- Where the data went (destination IP, system name).
- What the outcome was (success or failure).
This isn't just for show. This is your first line of defense when investigating an incident and your proof of due diligence if regulators come knocking.
While encryption is now the standard, adoption isn't where it should be. Some reports indicate that by 2025, only about 62% of organizations will have a formal encryption strategy for file sharing. That leaves a huge gap.
This is why forward-thinking organizations are embracing a zero-trust security model. The old "castle-and-moat" approach is dead. Zero trust assumes threats can come from anywhere—even from inside your own network—and requires strict verification for every single request.
This mindset, combined with the fact that the secure file transfer market is projected to hit $3.63 billion by 2029, shows a clear industry shift toward more rigorous security. The zero-trust philosophy perfectly complements your technical controls, creating a much more resilient and secure environment for every piece of data you handle.
Implementing Your Human and Procedural Safeguards

Even with the best technology, a HIPAA compliant data transfer isn't guaranteed. The most advanced encryption in the world can be completely undone by one well-meaning employee making a simple mistake. This is exactly why your human and procedural safeguards are so critical—they are the policies, training, and people that form the real foundation of your compliance program.
Think of these safeguards not as red tape, but as the building blocks for a culture of security. When every person on your team truly understands their role in protecting patient data, you've built something strong and resilient. It all begins with taking an honest, hard look at your current processes.
Conduct a Meaningful Risk Assessment
Before you can write effective policies, you have to know where your weak spots are. A risk assessment for your data transfer workflows isn't some theoretical checklist; it's a practical hunt for potential points of failure.
Don't just run a generic audit. Get specific. For example, trace the entire journey of a single MRI file, from the moment it leaves the imaging machine to when it lands on a radiologist’s remote workstation.
- How does the file get from the modality to the local server?
- Who can access that server?
- What tool is used to send it to the external radiologist?
- How do you confirm the radiologist’s identity before they can download it?
By walking through these real-world scenarios, you'll uncover the hidden risks that audits often miss—things like a shared password for a download portal or using personal email as a "quick fix" for a failed transfer. These are precisely the gaps a proactive risk assessment is meant to find and close.
Enforce the Minimum Necessary Rule with Clear Policies
HIPAA’s "minimum necessary" rule sounds simple, but it's often tricky to get right in practice. The principle is that employees should only see the specific PHI they absolutely need to do their jobs. Vague policies are the enemy here.
Your access control policies need to be crystal clear. Don't just write "limit access to authorized personnel." You have to define who is authorized for what data and why.
For instance, a billing clerk needs patient demographic and insurance details, but they have no business viewing clinical notes or diagnostic images. Your data transfer system must be configured to enforce that separation.
A common point of failure I see is the "super user" account with keys to the entire kingdom. Limiting these accounts and properly implementing role-based access controls (RBAC) are essential for truly enforcing the minimum necessary standard with every HIPAA compliant data transfer.
This is more important than ever. Though HIPAA was enacted way back in 1996, the road to securing digital health data has been a long one. A surprising number of healthcare organizations still haven't appointed a dedicated HIPAA Privacy Officer with the authority to enforce these policies. And with up to 70% of organizations now using secure file transfer solutions, the technology has often leaped ahead of the written policies needed to govern it, creating serious compliance gaps. You can dive deeper into these trends in the 2025 HIPAA Journal Annual Survey results.
Empower Your HIPAA Privacy and Security Officers
The people you designate as your HIPAA Privacy and Security Officers can't just be names on a document. These roles need to be filled by individuals who have the genuine authority to implement, monitor, and enforce your security procedures. Think of them as your compliance champions.
These officers need a direct line to leadership and the budget to be effective. Their core responsibilities should always include:
- Overseeing routine risk assessments.
- Developing and updating all security and privacy policies.
- Managing the workforce training program.
- Investigating and leading the response to any potential security incident.
- Ensuring all Business Associate Agreements are up-to-date and followed.
Without this backing, your compliance program is just a paper tiger.
Build Training That Actually Sticks
Let's be honest: that once-a-year, check-the-box HIPAA training isn't cutting it. For training to work, it has to be ongoing, relevant, and engaging. Your team doesn’t need to memorize the HIPAA text. They need to know how to handle the real situations they face every single day.
Focus your training on the threats that matter most for data transfer:
- Phishing Scams: Run simulations to teach staff how to spot a malicious email trying to steal credentials for your secure transfer portal.
- Unapproved Devices: Have a clear, firm policy on transferring PHI with personal laptops or phones and explain the "why" behind the risks.
- Social Engineering: Train your front-line staff to verify any request for PHI that comes in over the phone or email before sending anything.
Finally, don't forget to secure the physical endpoints. A locked server room is a classic physical safeguard, but so is a simple privacy screen on a monitor in a high-traffic area. Make sure workstations used for data transfers automatically lock after a few minutes of inactivity and are positioned to prevent nosy "shoulder surfing." These small, practical steps are just as vital as any high-tech solution.
Mastering Business Associate Agreements for Data Transfer
All your technical safeguards and internal policies are crucial, but they don't operate in a silo. The second you bring a third-party vendor into the mix—whether it's a cloud storage provider or a specialized medical imaging platform—your compliance responsibilities stretch to include them. This is precisely where the Business Associate Agreement (BAA) becomes one of your most critical assets for a HIPAA compliant data transfer.
Let's be clear: a BAA is not just a checkbox item. It's a legally binding contract that makes your partners accountable to the same HIPAA rules you are. If you don't have a signed BAA from every single vendor that touches, stores, or transmits PHI on your behalf, you are non-compliant. It’s that black and white.
But getting a signature is just the start. The real work is making sure the BAA actually protects you and then thoroughly vetting the vendor behind it.
Decoding the BAA for Data Transfer
When you're handed a BAA from a tech partner, especially one involved in data transfer, some clauses are absolutely non-negotiable. You can't just skim it. You need to look for specific, crystal-clear language that protects your organization and, most importantly, your patients' data.
A generic line about "maintaining security," for example, is far too weak. What you need are explicit commitments. A solid BAA will spell out the business associate's duties for everything from their encryption standards to exactly how they’ll respond to a data breach.
I’ve seen organizations get into serious hot water by blindly accepting a vendor’s one-page, boilerplate BAA. A proper BAA for a data transfer service should be a detailed document that leaves zero room for misinterpretation of their security obligations.
A vague agreement is a massive liability. If a breach happens on their watch, a well-drafted BAA ensures they are contractually—and financially—on the hook for the fallout, including notification costs and potential fines.
Essential Clauses for Every Data Transfer BAA
When you're dealing with partners like PYCAD that handle something as sensitive as medical imaging data, your BAA needs to be especially robust. The agreement must match the complexity of the information being shared.
Here's a practical checklist of what I always insist on:
- Explicit Encryption Requirements: The contract must state that all PHI will be encrypted both in transit (using protocols like TLS 1.2 or higher) and at rest (using strong algorithms like AES-256).
- Strict Breach Notification Timelines: The BAA must force the vendor to notify you of any security incident without "unreasonable delay." I recommend specifying a hard deadline, like within 24 or 48 hours, so you can meet your own reporting obligations.
- Subcontractor Liability (The "Chain of Trust"): This is a big one. The agreement must make the business associate responsible for ensuring their subcontractors who handle your PHI also comply with HIPAA and sign their own BAAs.
- Audit and Access Rights: You need the contractual right to audit the vendor's security controls or, more practically, to receive their third-party audit reports (like a SOC 2 Type II) to verify their claims.
- Data Destruction Protocols: The agreement has to outline how the vendor will securely and permanently destroy all of your PHI when your contract ends.
Updating BAAs for New National Security Rules
As we’ve covered, HIPAA isn't the only regulation you need to worry about anymore. New federal rules now restrict the transfer of sensitive data, including PHI, to certain foreign countries. Your BAAs must be updated to address this.
This means adding specific language that explicitly forbids the business associate and their subcontractors from moving your data to prohibited nations. For example, your BAA should include a clause like, "Business Associate agrees not to transfer or permit access to any PHI from a country of concern as defined under IEEPA regulations."
Leaving this out doesn't just violate these new rules; it creates a major national security compliance gap for your organization. Vetting a partner for a HIPAA compliant data transfer now requires asking pointed questions about where their data centers are and what their global data processing policies look like.
Avoiding Common Mistakes in PHI Transfer
Even with the best of intentions, the road to a fully HIPAA compliant data transfer is littered with potential pitfalls. It’s one thing to know the right steps, but it’s just as important to recognize the common mistakes that trip people up. These errors often come from taking shortcuts for convenience, holding onto outdated habits, or simply not understanding the very real risks involved.
The most glaring mistake I see time and again is using consumer-grade tools for professional healthcare work. Sending a patient's medical records through a personal Dropbox account or a free file-sharing service is a fast track to a data breach and a HIPAA fine. These services almost never come with a Business Associate Agreement (BAA) and simply don't have the necessary audit controls or encryption standards.
Along the same lines, sending PHI through unencrypted email is a surprisingly common misstep. Someone on your team might think it's a quick, harmless way to share a single report. In reality, an unencrypted email is like a postcard—anyone who intercepts it can read it. That one simple action can have serious financial consequences.
Failing to Automate and Monitor Consistently
Another major oversight is neglecting to automate routine data transfers. When a staff member has to manually drag and drop files into an SFTP client every day, human error is practically guaranteed. A simple distraction could send files to the wrong recipient or mean they aren't sent at all, which disrupts patient care and punches holes in your compliance.
Automating these workflows takes the human variable out of the equation, ensuring everything is consistent and reliable. It also frees up your team to focus on patient-centric tasks instead of repetitive data shuffling.
Just as critical is the lack of ongoing, active monitoring. Too many organizations set up their secure transfer systems and then just let them run without ever checking the audit logs. Those logs are your security cameras—they show you who is accessing what data and when. Without a regular review, suspicious activity can go unnoticed for weeks, if not months.
The goal isn't just to have logs for a potential audit; it's to use them proactively. Effective monitoring allows you to spot unusual patterns, like a user downloading an abnormally large volume of files, which could be an early warning sign of an internal threat or compromised account.
Automated auditing is worlds more effective than manual spot-checks. The data from automated systems paints a clear picture of just how much more secure and efficient they are.
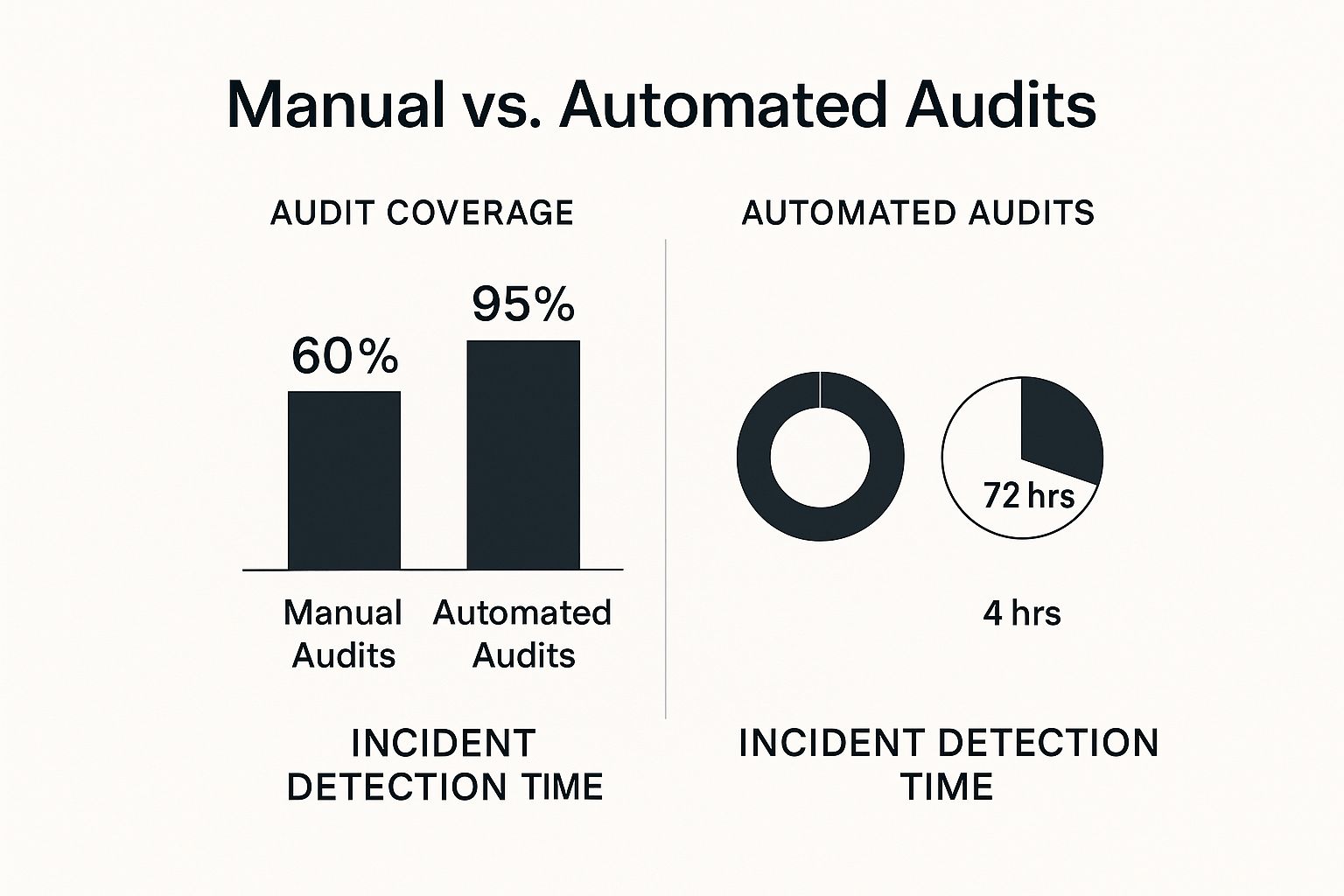
The numbers speak for themselves. Automation delivers nearly complete audit coverage at 95% and shrinks incident detection time from days down to a matter of hours.
De-Identification and Incident Response Blind Spots
Failing to properly de-identify data is another common stumble, especially when it comes to research or analytics projects. A lot of people mistakenly think that just scrubbing a patient's name and address is good enough. True de-identification is a much more complex statistical process. If you leave enough indirect identifiers in the dataset, it can be surprisingly easy to re-identify an individual, turning what you thought was "safe" data into a major PHI exposure.
Finally, having a generic incident response plan just won't cut it. You need a specific, battle-tested plan for breaches involving data in transit. Ask yourself:
- What's the immediate first step if your SFTP server is compromised?
- Who is responsible for shutting down access?
- How will you notify affected parties if an encrypted file transfer is intercepted and you think the encryption key was stolen, too?
Without pre-defined answers to these questions, your team will be scrambling during a crisis, losing precious time and likely making the situation worse.
To make this crystal clear, here’s a look at some everyday situations and the difference between a risky shortcut and a compliant, professional approach.
Compliant vs. Non-Compliant Data Transfer Scenarios
| Scenario | Non-Compliant Action | HIPAA Compliant Action |
|---|---|---|
| Sharing scans with a specialist | Attaching a DICOM file to a standard email. | Using a secure, BAA-backed medical imaging platform or SFTP server with end-to-end encryption. |
| Sending billing data to an insurer | Uploading a patient list to a personal cloud storage account and sharing the link. | Automating the transfer via a dedicated SFTP connection with the insurer, with full audit logging enabled. |
| Providing data for a research study | Removing only patient names before sharing a dataset via an unsecure method. | Following the HIPAA Safe Harbor method for de-identification and transferring the data via an encrypted, access-controlled channel. |
Steering clear of these common mistakes is absolutely fundamental to building a trustworthy and secure system for every HIPAA compliant data transfer. It all comes down to a commitment to using the right tools, enforcing strong procedures, and nurturing a culture of security awareness across your entire organization.
Got Questions About HIPAA Data Transfers? Let's Clear Things Up.
Even the most buttoned-up data transfer strategy runs into a few head-scratchers. When it comes to HIPAA compliance, there are always those "what if" scenarios that pop up and cause confusion. This is where we get into the nitty-gritty of some of the most common questions I hear from healthcare organizations trying to do the right thing with their data.
Think of this as your go-to guide for those practical, real-world questions. I'll give you straight, actionable answers to help you stay compliant and confident.
Can We Really Use Email to Send PHI?
This is easily the most common question, and the answer isn't a simple yes or no. Standard, out-of-the-box email is absolutely not HIPAA compliant. Sending patient information through a regular email account is like mailing a postcard with a diagnosis written on the back—anyone can read it along the way. It’s a huge, avoidable risk.
So, does that mean email is off the table completely? Not necessarily. You can use email, but only if you're using a specific, secure email service. These platforms encrypt the message from the moment you hit "send" until the recipient opens it, which often involves them logging into a secure portal. Without that end-to-end encryption, stick to a different method for transferring PHI.
Is SFTP Inherently HIPAA Compliant?
No, just flipping on an SFTP server doesn't magically make you compliant. While Secure File Transfer Protocol (SFTP) is a great starting point because it encrypts data while it's moving, that’s just one piece of the puzzle.
To truly make your SFTP setup part of a HIPAA compliant data transfer system, you need to build more security around it. Think about:
- Access Controls: Who can log in? Are their permissions limited to only what they need to see? You need strong passwords and role-based access.
- Audit Logs: Your system needs a detailed paper trail. It must log every single action—who logged in, what files they touched, and when. This is non-negotiable for security and accountability.
- Data at Rest Encryption: What happens to the files sitting on the server? Any PHI stored there, even for a minute, must also be encrypted.
- Business Associate Agreement (BAA): If a third-party hosts your SFTP server, you absolutely must have a signed BAA with them.
An SFTP server without these controls is just a tool, not a compliant solution.
I always tell people to think of it like this: owning a fireproof safe doesn't make your whole house fireproof. SFTP is the safe—it's strong. But you still need smoke detectors, fire extinguishers, and an evacuation plan (your policies and controls) to protect everything else.
What’s the Deal with De-identified and Anonymized Data?
This one trips a lot of people up. The assumption is that once you "anonymize" data, HIPAA rules no longer apply. That's true, but the key word is properly de-identified. HIPAA has a very strict definition of what that means.
You have two paths to de-identification under HIPAA:
- Expert Determination: A qualified statistician analyzes the data and confirms that the risk of re-identifying a person is incredibly small.
- Safe Harbor: This method is more black and white. You have to remove 18 specific identifiers, including things you'd expect like names and social security numbers, but also less obvious ones like specific dates and detailed geographic information.
Just deleting a patient's name isn't enough. If there's any reasonable way to link that data back to an individual, it's still considered PHI, and all the HIPAA transfer rules apply. When in doubt, always treat the data as protected.
At PYCAD, we live and breathe the complexities of medical imaging data. We make sure every single step, from anonymizing data for AI training to deploying a finished model, is handled with the highest level of security and compliance in mind. Our deep experience in AI and computer vision means we build solutions that stand up to the toughest healthcare regulations. Find out how we can help your project at PYCAD.