Medical device software testing is the methodical process of verifying and validating software that powers medical devices. It’s about making sure that software is safe, effective, and fully compliant with a web of global regulations.
Think of it this way: a pharmacist meticulously double-checks a prescription before handing it over. In the same vein, the software guiding a surgical robot or an insulin pump must be flawless. There's simply no room for error when a patient's health is on the line.
Why Medical Device Software Testing Is So Critical

In today's healthcare, software isn't just a background feature; it's often the very brain of a medical device. It interprets diagnostic images, controls life-sustaining equipment, and manages patient data. Flawless operation isn't just a goal—it's a non-negotiable requirement for patient safety. This is why medical device software testing isn't just another box to check on a development timeline; it's a cornerstone of public health.
The stakes are incredibly high. With consumer software, a bug might be a minor annoyance. But a glitch in medical software can lead to a misdiagnosis, an incorrect treatment, or a catastrophic equipment failure. The complex interplay between software, hardware, and the human user creates an environment where even a tiny defect can have devastating consequences.
The Foundation of Trust and Compliance
Rigorous, documented testing is what builds trust between patients, clinicians, and regulatory bodies like the FDA. When a device gets cleared for the market, it carries an implicit promise of exhaustive scrutiny. This scrutiny is what prevents patient harm and ensures the device does what it's supposed to do, reliably, every single time.
This entire process is deeply rooted in the principles of Quality Assurance (QA), which must be woven into the entire development lifecycle. It's about creating a documented, evidence-based trail that proves the software is not only effective but, above all, safe.
The goal isn’t just to find bugs. It's about methodically proving that the software meets all requirements and that every conceivable risk to patient safety has been identified, controlled, and mitigated.
A Rapidly Growing Field
As medical devices become more complex and global regulations get stricter, this specialized field has seen significant growth. This trend underscores the industry's deep commitment to safety and the public's demand for advanced, trustworthy healthcare technology.
The global market for medical device software testing services was recently valued at around USD 1.5 billion and is expected to climb to nearly USD 3.4 billion, with a compound annual growth rate of 8.5%. This expansion is fueled by new technologies like AI and machine learning, which introduce new complexities and require entirely new levels of validation to prove their accuracy and reliability.
Ultimately, there is only one path to bring a safe, effective, and compliant medical device to the people who need it: comprehensive testing. It’s the bedrock on which all modern healthcare innovation is safely built.
Decoding the Global Regulatory Framework

Diving into the world of medical device software regulations can feel like trying to translate a complex legal document written in a dozen different languages. For anyone building this kind of technology, these rules aren't just red tape; they are the fundamental blueprints for creating safe, effective, and reliable products. They ensure that every piece of software is built using a repeatable, quality-driven, and meticulously documented process.
At the core of this global framework are a handful of key standards and governing bodies. You don't need to memorize every line of every regulation. Instead, the goal is to get fluent in the core principles that drive them all: safety, risk management, and traceability.
Getting this right is also a huge competitive advantage. The global medical device testing services market was recently valued at USD 9.76 billion and is projected to hit USD 16.78 billion soon. That growth is fueled by increasingly complex products and the tough approval standards that make rock-solid testing a non-negotiable part of the process.
Key Standards That Shape Medical Device Software
While there are many regulations out there, a few are foundational to medical device software testing across the globe. Think of them as the shared rulebook for how to manage the software lifecycle, ensuring quality is baked in from the very first line of code.
- IEC 62304: This is the big one—the primary international standard for how medical device software should be developed, tested, and maintained. It sorts software into safety classes (A, B, or C) based on risk and lays out the specific activities required for each.
- ISO 13485: This standard is all about the bigger picture: your Quality Management System (QMS). It ensures you have documented, repeatable processes for everything from design and development to production and testing.
- FDA 21 CFR Part 820: This is the U.S. Food and Drug Administration's version of a QMS, known as the Quality System Regulation. It’s very similar in spirit to ISO 13485 and demands strict design controls, which absolutely include software validation and risk analysis.
These standards don't exist in a vacuum; they work together. If you think of IEC 62304 as the standard telling you what to do with your software, then ISO 13485 and 21 CFR 820 define the quality system that dictates how you must do it.
Understanding Software as a Medical Device
A pivotal concept to grasp is Software as a Medical Device (SaMD). This isn't software that simply runs on a physical device; it is the device. We're talking about mobile apps that analyze X-rays for signs of disease or cloud-based platforms that calculate precise medication dosages.
The International Medical Device Regulators Forum (IMDRF) provides a framework for classifying SaMD based on the risk it poses to patients. This classification is incredibly important because it directly determines the depth of testing and documentation you'll need for approval. A low-risk wellness app will face far less scrutiny than a high-risk diagnostic tool that informs life-or-death decisions.
The guiding principle is refreshingly simple: the greater the potential harm from a software failure, the more rigorous your testing and documentation must be. This risk-based approach ensures that time and resources are focused where they matter most—on protecting patient safety.
A cornerstone of regulatory adherence is maintaining consistency. Establishing clear Standard Operating Procedures (SOPs) is essential for this. If you're looking for a good starting point, resources like these Standard Operating Procedure Templates can be incredibly helpful.
FDA vs. EU MDR: A Simplified Comparison
While global standards like IEC 62304 create a lot of harmony, different regions still have their own specific rules. For any company looking to launch a product in both the United States and Europe, understanding the nuances between the FDA and the EU’s Medical Device Regulation (MDR) is critical.
Here’s a look at how their requirements stack up in a few key areas for software.
Key Regulatory Requirements for Medical Software
| Requirement Area | FDA (United States) | EU MDR (European Union) |
|---|---|---|
| Risk Classification | Uses a three-tiered system (Class I, II, III). Software risk is often linked to the parent device's class. | Uses a rule-based system (Class I, IIa, IIb, III). SaMD has its own specific classification rules under Rule 11. |
| Documentation | Requires a Design History File (DHF) to document the entire design and development process, including all testing. | Mandates a Technical Documentation file that must be a "living document," continuously updated throughout the device's lifecycle. |
| Post-Market Activities | Emphasizes medical device reporting (MDR) for adverse events and potential product corrections or recalls. | Requires a robust Post-Market Surveillance (PMS) plan and Periodic Safety Update Reports (PSURs) for higher-risk devices. |
At the end of the day, both the FDA and EU regulators are chasing the same outcome: a well-documented, risk-managed, and thoroughly tested software product that is proven to be safe and effective for patients.
Building Your Software Testing Lifecycle
Effective testing for medical device software isn't just a single action you take before launch; it's a comprehensive, continuous process that runs parallel to the entire development journey. This is what we call the software testing lifecycle. It creates a structured, repeatable, and—most importantly—auditable path from the initial concept all the way to market release and post-market surveillance.
Think of it this way: you wouldn't build a bridge by just pouring concrete and hoping for the best. You'd start with a detailed blueprint, test the strength of every beam, and ensure every connection is secure before letting traffic cross. The software testing lifecycle is that blueprint for quality and safety. It ensures every piece of the software is checked individually before being connected, and that the final system performs exactly as intended in the real world.
This methodical approach is what stops critical safety features from slipping through the cracks. It moves testing from an afterthought to a core activity that informs and validates development at every stage.
The Foundational Stages of Testing
The testing lifecycle isn't one giant, monolithic task. It’s intentionally broken down into distinct stages, each with its own specific goal. This layering is crucial because it helps teams find problems early, which is always cheaper and easier than fixing them right before a product release.
Here’s a breakdown of the key stages:
-
Test Planning and Requirements Analysis: This is the blueprint phase. Here, the team maps out the entire testing strategy, defining the scope and objectives. They meticulously dig into the software requirements to figure out what, exactly, needs to be tested. Every single user need and safety feature must be turned into something that can be verified.
-
Test Case Design and Development: With the "what" clearly defined, the team moves on to the "how." They write detailed test cases—these are essentially step-by-step scripts for testers to follow, complete with specific inputs and the precise outcomes they should expect to see. This is where the high-level plan becomes a set of practical, actionable instructions.
-
Test Execution and Defect Reporting: This is where the rubber meets the road. Testers run the prepared test cases, carefully comparing what actually happens with what should happen. Any time there's a mismatch (a bug), it gets logged in a defect tracking system. This report includes all the details a developer needs to find the problem, replicate it, and fix it for good.
-
Test Reporting and Closure: Once a testing cycle is finished, the team pulls together a complete test summary report. This document gives stakeholders a clear snapshot of the entire effort: what was tested, what passed, what failed, and a final assessment of the software's quality. This report is a non-negotiable piece of evidence for your regulatory submissions.
This flow, from small components to the whole system, is often visualized as a bottom-up process.
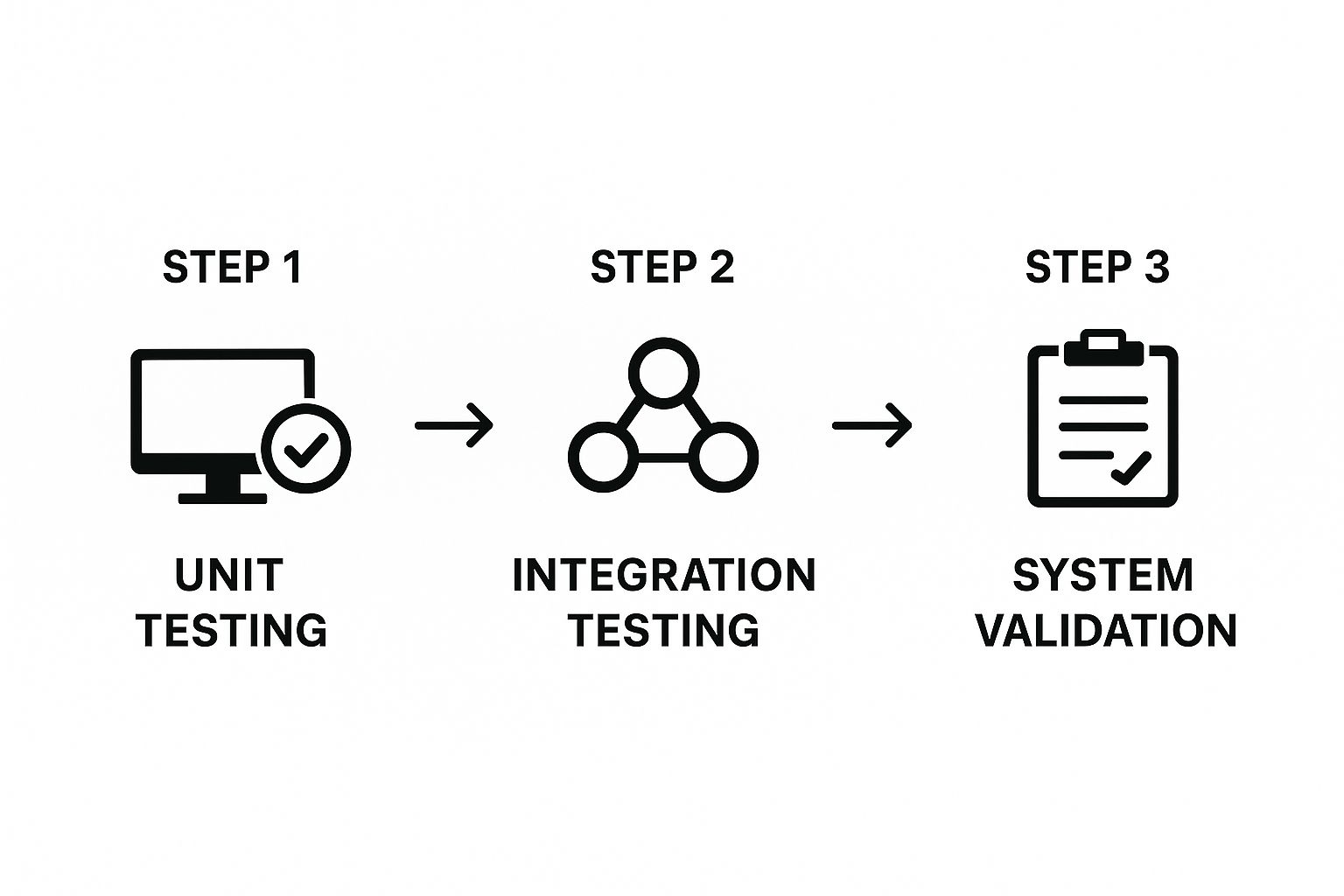
As the infographic shows, confidence is built layer by layer. You prove the small things work before you move on to the more complex, integrated stages.
The Unbreakable Chain of Traceability
Within this lifecycle, one concept stands above all others: traceability. For regulators like the FDA, it’s not good enough to just say you’ve tested everything. You have to prove it with an unbroken documentary chain.
Traceability is the documented ability to connect every single software requirement to its design specification, its code, and, most critically, to the specific test case that confirms it works as intended. This creates a crystal-clear, auditable trail that proves you've achieved complete test coverage.
Let’s take a simple example. Imagine a user requirement states, "The device must sound an alarm if the battery level drops below 10%." A solid traceability matrix would create a link from this requirement to:
- The software design document that details the alarm's logic.
- The specific function in the source code that triggers the alarm.
- The exact test case written to simulate a low-battery event and confirm the alarm sounds correctly.
- The final test report showing that this specific test was executed and passed.
This meticulous linking is the absolute cornerstone of compliant medical device software testing. It provides the objective evidence that no requirement was forgotten and that every risk identified during design has been properly tested and mitigated. Without it, your regulatory submission is simply incomplete.
Of course. Here is the rewritten section with a more natural, human-expert tone.
Core Testing Methods You Need To Know
When it comes to medical device software, you can't just run a few tests and call it a day. Ensuring a device is safe and effective requires a strategic mix of testing methods, each looking at the software from a unique perspective. This is how we find and squash bugs before they have any chance of affecting a patient.
At the highest level, every test we run falls into one of two buckets: Verification and Validation (V&V). People often use these terms interchangeably, but in the world of medical devices, they answer two distinct and equally vital questions.
I like to use a simple analogy: baking a cake for a customer.
- Verification is all about checking your work against the recipe. Did you use the right amount of flour? Did you mix the ingredients in the correct order? Did you bake it at the right temperature? In software terms, verification asks: "Did we build the product right?"
- Validation is the taste test. After you've followed the recipe to the letter, you give the finished cake to the customer. Is it what they actually wanted? Is it delicious? Does it meet their expectations? For software, validation asks: "Did we build the right product?"
You absolutely need both. Building a flawless piece of software that doesn't solve the user's problem (verification without validation) is a waste of effort. On the other hand, creating a product that users want but is riddled with bugs (validation without verification) is downright dangerous.
The Different Layers of Testing
Think about how you'd build a house—you start with the foundation and work your way up. Software testing follows a similar layered approach. Each layer builds on the last, moving from detailed checks of tiny code components to a complete evaluation of the final product.
Unit and Integration Testing
Everything begins at the smallest scale with unit testing. This is where developers put individual pieces of code—a single function or component—under a microscope to see if they work in isolation. For an infusion pump, a unit test might check if the function that calculates a drug's dosage rate returns the correct number when given specific inputs. It's the first line of defense to make sure the basic building blocks are sound.
Next, we move on to integration testing. This is where those individual units are combined and tested as a group. This step is crucial because it uncovers problems that only surface when different parts of the software start communicating with each other. For example, does the dosage calculation module correctly pass its result to the component that controls the pump's physical motor?
Catching defects at these early stages is a huge win—it’s when they are cheapest and easiest to fix.
System and Acceptance Testing
Once all the individual pieces have been brought together, it's time for system testing. This is the first time we test the entire software system as a complete, integrated whole. Testers essentially treat the software as a "black box," running it through real-world scenarios to confirm it meets every requirement. For something complex like an MRI machine, system testing ensures the control software, imaging algorithms, and user interface all work together without a hitch.
The final hurdle is User Acceptance Testing (UAT). This is a form of validation where the software is put into the hands of the people who will actually use it—clinicians, nurses, or lab technicians. They test it in their own environment to confirm it not only works but also meets their practical needs. Their sign-off is the ultimate proof that you built the right product for the right people.
Essential Types of Non-Functional Testing
Checking that features work is only part of the story. We also have to be sure the software is reliable, secure, and user-friendly. That requires a few specialized tests.
- Usability Testing: This makes sure clinicians can operate the device easily and intuitively, especially under the high-pressure conditions of a real hospital.
- Security Testing: Here, we actively try to break in. The goal is to find and patch vulnerabilities to protect sensitive patient data and prevent anyone from tampering with the device.
- Performance Testing: This confirms the software responds quickly and remains stable, even when it’s being pushed to its limits.
The intense focus on these methods is reflected in the market's growth. The entire medical device testing market, including software, was valued at around USD 10.76 billion and is expected to climb to nearly USD 23.95 billion. This boom is fueled by strict regulations and the unwavering demand for safe, high-quality medical equipment. You can discover more about the expanding medical device testing market and what's driving it.
By layering these different methods, you build a comprehensive testing strategy. It’s a systematic approach that leaves no stone unturned and builds a powerful case that your software is both safe and effective for patient use.
Selecting the Right Tools for Compliance and Efficiency

Let's be honest: your testing strategy is only as effective as the tools you use to bring it to life. Picking the right toolkit isn't just a matter of making your team faster. It’s about building a solid, auditable system that proves you’ve met every quality and compliance benchmark.
The days of relying on spreadsheets and manual checklists are long gone. To keep up with today's stringent regulatory demands, you need a connected ecosystem of tools. This digital toolkit becomes your living, breathing proof of compliance, linking every requirement to a final test report and giving you the confidence—and the evidence—to stand behind your product's safety.
Core Categories of Testing Tools
Putting together the right testing environment means looking at a few essential software categories. Each one has a specific job to do, and together, they create a safety net to ensure nothing falls through the cracks.
A solid setup will almost always include tools for:
- Requirements and Test Management Platforms: Think of these as the mission control for your entire quality process. Tools like Jama Connect or Jira are where you document requirements, connect them directly to test cases, and track the entire workflow. This provides the end-to-end traceability that regulators absolutely require.
- Automated Testing Frameworks: Automation is your best friend when faced with a mountain of tests. It's simply not feasible to cover everything manually. Frameworks like Squish for GUI testing or GoogleTest for C++ unit tests can simulate thousands of user actions and check code behavior far more rapidly and reliably than any human team.
- Static Analysis Tools: These tools are like an expert proofreader for your code, but instead of grammar, they're hunting for security vulnerabilities, potential bugs, and violations of coding standards. The best part? They find these issues before the software is ever run, saving you headaches down the line.
Investing in the right tools is an investment in your compliance posture. A good tool doesn't just find bugs; it generates the documentation and audit trails that prove to regulators that your software development process is under control and your device is safe.
Key Criteria for Choosing Your Tools
With so many options on the market, how do you choose? It’s easy to get distracted by flashy features. The real test is how well a tool supports the specific, high-stakes demands of medical device development.
When you're evaluating any potential tool, these are the make-or-break criteria:
- Support for FDA 21 CFR Part 11: This is a dealbreaker. The tool must have built-in features for electronic records and electronic signatures to ensure data integrity. It’s a foundational FDA requirement.
- Clear Audit Trail Capabilities: The software needs to automatically create a permanent record of who did what, and when they did it. This immutable log is exactly the kind of evidence auditors want to see.
- Seamless Integration: Your tools can't live in silos. Your test management platform must talk to your automation frameworks, which in turn must connect to your team’s version control system (like Git). A unified workflow is the goal.
- Risk Management Features: The best tools let you directly link your test cases back to the risks you identified in your ISO 14971 analysis. This is incredibly powerful—it helps you focus your testing on the highest-risk functions and proves you’ve addressed every known hazard.
Selecting tools with this DNA will do more than just improve your medical device software testing process. It will build a much stronger, more defensible case for your product’s safety and compliance.
Proven Best Practices for Testing Success
Knowing the rules and methods is one thing, but actually putting them into practice for consistent results is a whole different ball game. Truly effective medical device software testing isn't just about running a series of technical checks; it’s about fostering a deep-rooted culture of quality. The companies that get this right are the ones that weave best practices into every single part of their software development lifecycle.
The foundation of this whole approach is built on a risk-based mindset. Think of it like performing medical triage on your own software. Instead of testing every single feature with the same level of intensity, you pour your most rigorous efforts into the areas where a failure could lead to the most severe patient harm. A bug in a dosage calculation algorithm, for instance, requires exponentially more attention than a simple typo in a help menu.
This core principle, which is heavily guided by standards like ISO 14971, ensures that your valuable time and resources are directed where they matter most: safeguarding patient safety.
Build Quality In, Don’t Inspect It On
The outdated model of developers building software and then tossing it over the wall to the QA team is fundamentally flawed, especially in a field as critical as medical devices. You can't just "inspect" quality at the end. It has to be an essential ingredient from the very first line of code.
This means shifting your entire team's perspective:
- Developers own their quality by writing unit tests for their code, creating the very first line of defense against bugs.
- Static analysis tools are built directly into the development pipeline, acting as an automated guard that flags potential issues before they become real problems.
- Peer code reviews become a standard, non-negotiable step, allowing for knowledge sharing and catching mistakes early.
When quality becomes a shared responsibility, you stop defects from ever happening in the first place. It's a classic case of fire prevention versus firefighting—and far more efficient.
Document Meticulously and Tell a Story
In the medical device world, there's a simple rule: if you didn't document it, it never happened. Your documentation isn't just a pile of paperwork; it's the complete narrative that proves your product is safe and effective. It needs to tell a clear, logical story that an auditor can follow without a struggle.
Your test records, traceability matrices, and risk analysis files are the official evidence of your due diligence. They must be organized, complete, and audit-ready at all times, providing an unbreakable link from every user requirement to its final validation.
This level of meticulous record-keeping is non-negotiable. It proves you have control over your processes and provides the concrete, objective evidence you need for regulatory submissions to agencies like the FDA.
Embrace Automation for Regression Testing
Every time you update your software, you face a new risk: did the new feature break something that used to work perfectly? The process of re-testing existing functionality is called regression testing, and doing it manually is a recipe for slow, expensive, and error-prone work.
This is where automation becomes your secret weapon. Automated test scripts can execute thousands of regression checks overnight, giving your team rapid feedback. This frees up your human testers to focus on what they do best: complex, exploratory testing that requires creativity and critical thinking.
By pairing a solid change control process with automated regression testing, you can ensure every software update meets the same high bar for safety and effectiveness as the original release. To keep your processes sharp, it's also a great idea to track essential quality assurance metrics. These data points can shine a light on areas needing improvement and prove the value of your quality efforts over time.
Got Questions? We’ve Got Answers.
When you're dealing with medical device software, a lot of questions pop up. It's a complex field, and getting the details right is critical. Here are some of the most common questions we hear from development and QA teams, answered in plain English.
What’s the Real Difference Between Verification and Validation?
It’s easy to get these two mixed up, but the distinction is crucial. Think of it like building a house.
Verification is about checking your work against the blueprint. Did we build the walls where the plans said they should be? Are the electrical outlets installed according to the schematic? It's an internal check to make sure you built the software right.
Validation, on the other hand, asks if you built the right house for the family moving in. Does the layout work for their daily life? Is it safe for their kids? This step confirms the software actually meets the user's real-world needs in a clinical setting. You need both to get regulatory approval.
How Does Risk Management Fit into Software Testing?
Risk management isn't just a box-ticking exercise; it’s the very foundation of your testing strategy. Using a standard like ISO 14971, you start by figuring out what could possibly go wrong with the software and how it might harm a patient.
This risk analysis becomes the map for your testing efforts.
A high-risk feature, like the algorithm that calculates an insulin dose, will undergo the most intense, in-depth testing imaginable. A lower-risk function, like changing the color of the user interface, will get less attention. The key is that your documentation must show a clear line from every identified risk to the specific tests you ran to control it.
What Makes Testing SaMD So Different?
Testing Software as a Medical Device (SaMD) is a whole different ballgame. With traditional medical devices, the software runs on hardware you control. But SaMD often lives on a patient's own smartphone or in the cloud, which opens up a world of variables.
You're suddenly testing for a massive combination of factors:
- Operating Systems: Different versions of iOS, Android, and Windows.
- Hardware Chaos: Countless screen sizes, processor speeds, and memory specs.
- App Interference: What happens when another app on the user's phone tries to take over?
On top of that, since SaMD is always connected, cybersecurity isn't just a feature—it's essential. The fast-paced update cycles for apps also mean you need an incredibly tight process to re-validate every single new version to prove it’s still safe long after the initial release.
Do I Really Need to Test Every Piece of Software on My Device for IEC 62304?
Not exactly, but you are responsible for it. The IEC 62304 standard applies directly to the medical device software—the code your team actually writes.
However, most modern devices also include SOUP (Software of Unknown Provenance). This is just a formal name for any off-the-shelf software you didn't create, like a commercial operating system or a third-party code library.
Even though you didn't write the SOUP, you're on the hook for how it behaves in your device. Your job is to conduct a risk assessment on every SOUP component, figure out how it could fail, and then implement controls and tests to prove it won't jeopardize your device's safety or performance.
At PYCAD, we live and breathe this stuff. We specialize in building and validating the complex AI models at the heart of modern medical imaging software. Our experience helps ensure your product not only meets but exceeds the highest standards for safety and accuracy. Learn how we can help you navigate these challenges at https://pycad.co.