Data anonymization is all about stripping away personal details from a dataset so you can't trace anything back to a single person. It’s a bit like blurring out faces in a photo of a packed concert; you can still see how the crowd is behaving, but the individuals are completely unrecognizable. This is the bedrock of how we balance powerful data analysis with the fundamental right to privacy.
The Foundation of Data Privacy

At its heart, true data anonymization is designed to be a one-way street. The goal is to permanently break the connection between a piece of information and a real person. Once the data is properly anonymized, there’s no secret key or backdoor to reverse the process and reveal the original identities.
This makes it an incredibly powerful tool. It’s what allows researchers to sift through thousands of medical images to find patterns in disease progression or lets developers train their AI on real-world data without putting anyone's personal information at risk. Without this process, huge amounts of valuable data would be off-limits, locked down by privacy concerns.
Anonymization vs Pseudonymization
It's really important not to mix up anonymization with a related but different technique: pseudonymization. They both protect privacy, but they work in fundamentally different ways and are used for different reasons.
Pseudonymization is more like giving someone a secret codename. It swaps out direct identifiers—like a name or patient ID—with a consistent, artificial one (a "pseudonym"). The critical difference is that this process can be reversed. A separate, securely-held key can be used to link the data back to the original person.
Anonymization, on the other hand, erases the identity entirely. There’s no codename and no key to unlock the original information. It's gone for good.
This table offers a clear, side-by-side comparison to help you quickly grasp the crucial distinctions between anonymization and pseudonymization, focusing on reversibility, risk, and typical use cases.
Anonymization vs Pseudonymization Key Differences
| Characteristic | Anonymization | Pseudonymization |
|---|---|---|
| Reversibility | Irreversible; identifiers are permanently removed or altered. | Reversible; a key can re-link data to an individual. |
| Risk Level | Very low risk of re-identification if done correctly. | Higher risk, as the re-identification key is a major security target. |
| Typical Use Case | Releasing public datasets for open research. | Tracking a patient's progress in a clinical trial without using their name. |
Essentially, you anonymize data you want to share or analyze broadly without any possibility of re-identification. You pseudonymize data when you need to protect identities internally but might still need to link that data back to a specific person later on for legitimate, authorized reasons.
Why Data Anonymization Is No Longer Optional

It wasn't that long ago that data anonymization was a niche practice, something only the most forward-thinking organizations worried about. Today, it’s a non-negotiable part of doing business. This isn't just a trend; it's a fundamental shift driven by two major forces: iron-clad data privacy laws and the incredible potential locked away inside sensitive datasets.
The most immediate motivation for many is the very real, and very steep, cost of getting it wrong. Regulators worldwide have stopped asking nicely and are now enforcing strict data protection rules with massive financial penalties.
The High Stakes of Regulatory Compliance
Regulations like Europe’s General Data Protection Regulation (GDPR) and the U.S.’s Health Insurance Portability and Accountability Act (HIPAA) have redrawn the lines for handling personal data. These aren't just guidelines—they're legal mandates that carry serious weight.
A single GDPR violation, for example, can trigger fines of up to 4% of a company's global annual revenue. For a large corporation, that’s a potentially crippling blow. It’s no wonder that a solid understanding of what is data anonymization has become a cornerstone of modern risk management.
Properly anonymizing data is one of the surest ways to sidestep these risks. When information can no longer be tied to an individual, it often falls outside the scope of these stringent privacy laws. For a deeper dive into protecting data, especially in cloud environments, this guide to cloud data protection is a great resource.
Unlocking Business Value and Building Trust
But anonymization is much more than just a defensive play. When done right, it becomes a powerful tool for unlocking strategic value and innovation, allowing you to use and share data without putting privacy on the line.
Think about collaborative medical research or the development of complex AI algorithms. Anonymization allows institutions to pool massive datasets, leading to breakthrough discoveries and more accurate diagnostic tools, all while upholding their ethical duty to protect patient confidentiality.
The market is responding to this demand in a big way. Valued at USD 94.17 billion in 2025, the global data anonymization market is expected to skyrocket to USD 176.97 billion by 2030. This explosive growth shows just how critical these techniques have become for both security and progress.
Ultimately, a robust anonymization strategy does something invaluable: it builds trust. It tells your customers, patients, and partners that you take their privacy seriously. In an era of constant data breaches, that kind of trust is priceless.
Core Techniques for Anonymizing Your Data
So, how does data anonymization actually happen in the real world? It's less about a single magic button and more about choosing the right tool for the job. The best technique really hinges on what kind of data you're working with and what you hope to accomplish with it. Each method strikes a different balance between locking down privacy and keeping the data useful for analysis.
Let's imagine a simple patient record: it has a name, an exact age of 47, a specific zip code, and a diagnosis. We can use this as our guide to see how different techniques transform this sensitive information, making it safe to use for research without sacrificing its core value.
This image breaks down the key benefits of anonymization, highlighting how it protects privacy, preserves data utility, and ensures you're playing by the rules.
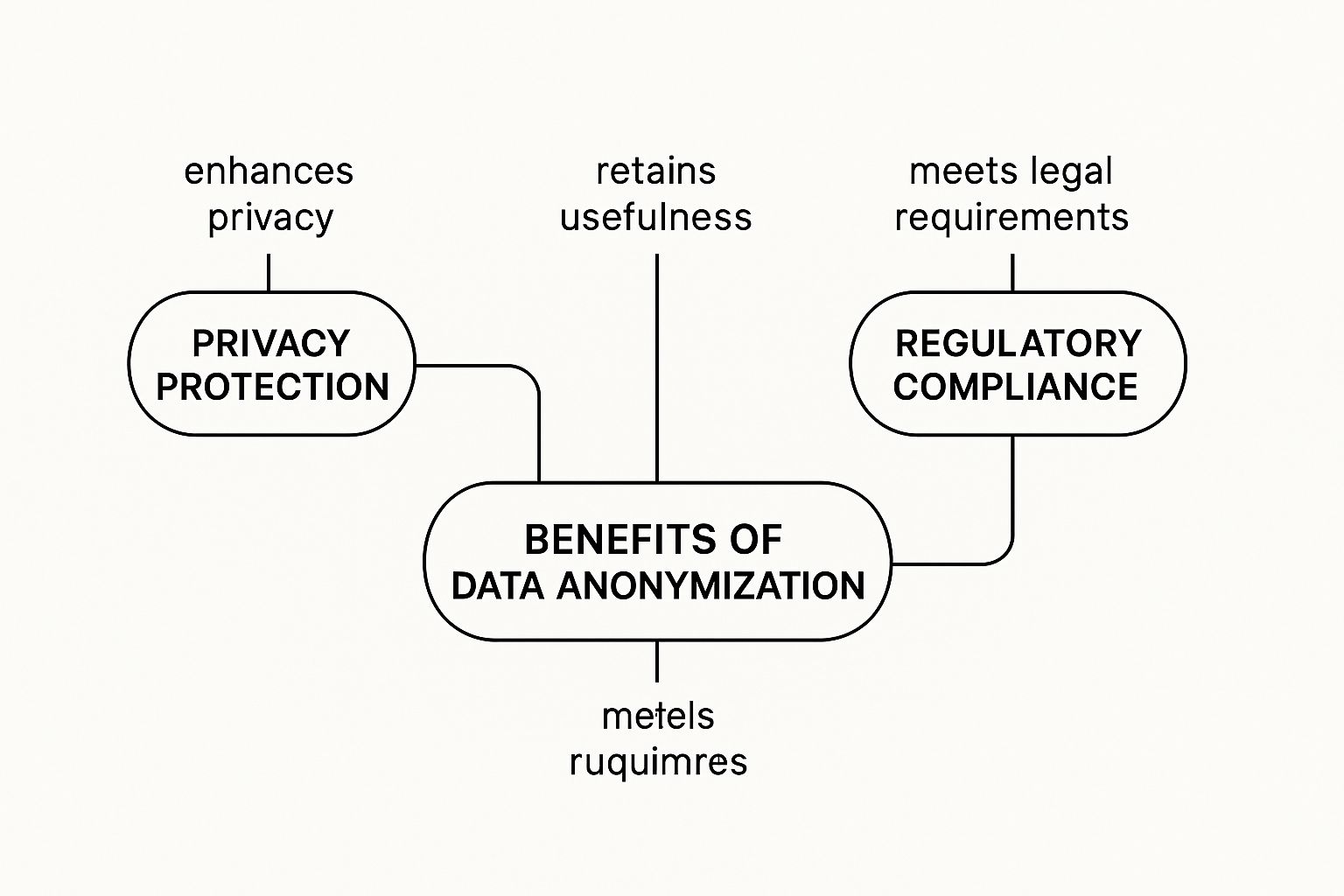
As you can see, these three elements are completely intertwined. They work together to build a data environment that's both secure and rich with insight.
Generalization and Suppression
Let's start with two of the most common and intuitive techniques: generalization and suppression. Think of them as the foundational tools in your anonymization toolkit. They're often used together to dial down the specificity of data that could easily point back to an individual.
-
Generalization: This is all about making data a little fuzzier. Instead of using our patient's precise age of 47, we would generalize it into a broader category, like the 40-50 age range. A specific zip code could be expanded to cover a whole city or county. It’s still useful, just less exact.
-
Suppression: This one is as straightforward as it sounds—you simply remove the identifier altogether. In our example, the patient's name would be completely deleted from the record. It’s often the very first step for getting rid of direct identifiers.
While these methods are effective and relatively simple to implement, they come with a trade-off. Blurring the data too much can reduce its analytical power. If a medical study needs to analyze outcomes for patients of a very specific age, generalization might not work. It's always a balancing act.
Data Masking and Perturbation
When you need the data to maintain a realistic structure and feel, you'll want to look at more sophisticated methods like data masking and perturbation. These techniques alter the data in clever ways.
Data masking is like giving your data a disguise. It swaps out sensitive information with fake, but structurally identical, data. Our patient's name could be replaced with a randomly generated but plausible-sounding name. This is incredibly valuable when creating datasets for software testing or training, where the data format has to be perfect. The global data masking market is expected to jump from USD 1.07 billion to USD 2.83 billion by 2033, which shows just how critical this technique has become. For a deeper dive into this trend, you can learn more about the data masking market growth.
Perturbation works differently by adding a bit of controlled statistical "noise." Instead of swapping data, it slightly modifies it. The patient's age might be nudged from 47 to 49, or down to 45. While any single record is now technically inaccurate, the overall statistical properties of the entire dataset remain intact. This makes it perfect for large-scale analysis or training machine learning models where the big picture matters more than the tiny details.
Comparing Data Anonymization Techniques
Choosing the right approach is a strategic decision. To help clarify which technique might fit your needs, this table breaks down the essentials of each method. It compares how they work, their best use cases, and the level of re-identification risk to help you make informed decisions for your data strategy.
| Technique | How It Works | Best For | Risk of Re-identification |
|---|---|---|---|
| Generalization | Reduces data precision by grouping it into ranges or broader categories (e.g., age 47 becomes 40-50). | Public data releases, statistical summaries, and situations where high precision isn't required. | Low to medium. Can be vulnerable to linkage attacks if not combined with other methods. |
| Suppression | Completely removes direct identifiers like names, addresses, or Social Security numbers from the dataset. | The first step in almost all anonymization processes to remove obvious personal information. | Low for direct identifiers, but indirect identifiers can still pose a risk. |
| Data Masking | Replaces sensitive data with realistic but fabricated data that maintains the original format. | Creating realistic datasets for software testing, development, and training environments. | Very low, as the original data is replaced. Risk depends on the quality of the masking. |
| Perturbation | Adds random statistical noise to numerical data, slightly altering individual values but preserving overall trends. | Large-scale statistical analysis, machine learning models, and scenarios where aggregate accuracy is key. | Low, especially in large datasets. Individual records are inaccurate, making re-identification difficult. |
Ultimately, there’s no one-size-fits-all answer. You have to weigh the risk, consider how the data will be used, and stay compliant with regulations to create a dataset that is both safe and powerful.
Navigating the world of data privacy regulations can feel like trying to solve a puzzle with half the pieces missing. For anyone working with medical data, two names stand out: HIPAA in the United States and GDPR in the European Union. These aren't just guidelines; they're the rulebooks that define how we must handle personal information.
Getting this right is non-negotiable. Falling short can lead to massive fines and a serious blow to your reputation. This is where anonymization comes in—it’s a practical way to meet these legal demands by fundamentally changing the data so it no longer points to a specific person.
HIPAA and the Safe Harbor Method
In the U.S. healthcare world, HIPAA offers a very direct, almost checklist-style, route to de-identifying data. It’s called the "Safe Harbor" method, and it’s straightforward: remove 18 specific identifiers, and the data is no longer considered Protected Health Information (PHI).
What kind of identifiers are we talking about? It's a comprehensive list designed to eliminate any obvious links to an individual.
- Names, of course, but also any geographic details smaller than a state.
- Specific dates tied to a person (birthdays, admission dates, etc.). You can keep the year, but that's it.
- Contact information like phone numbers, fax numbers, and email addresses.
- Unique identifiers like Social Security numbers or medical record numbers.
- Biometric data, from fingerprints to voice prints.
- Full-face photos or any other images that could identify someone.
Once all 18 of these are gone, the data is officially de-identified. This unlocks its potential for crucial work in research, analytics, and public health without stepping on privacy landmines.
GDPR's Broader Definition of Personal Data
Now, let's hop across the pond to Europe, where the GDPR takes a different, more expansive view. Instead of a checklist, GDPR operates on a core principle: personal data is any information that relates to an identifiable person.
This definition is intentionally broad. It’s not just about a name or social security number. An IP address, a device ID, or even certain location data could all fall under GDPR’s umbrella if they can be used to single out an individual.
This screenshot from the official GDPR information portal really drives home just how comprehensive the regulation is.
The key difference here is the focus on identifiability. If there's any reasonable way to link data back to a person, GDPR considers it personal data and its rules apply.
Under GDPR, truly anonymized data—where re-identification is effectively impossible—is no longer considered personal data. This means it falls outside the scope of most GDPR rules, giving organizations a huge incentive to get anonymization right.
It's no surprise, then, that the market for tools that help with this is booming. The global data masking tools market, currently valued at around USD 500 million, is expected to skyrocket to nearly USD 1.5 billion by 2032. As you can discover more insights about the data masking market on dataintelo.com, this explosive growth is a direct response to regulations like GDPR, which are pushing everyone to adopt smarter, more secure ways of handling information.
Navigating the Common Pitfalls of Anonymization
Putting data anonymization into practice is rarely a straightforward affair. It's less like flipping a switch and more like walking a tightrope. The biggest challenge? Striking the perfect balance between protecting privacy and keeping the data genuinely useful.
If you go too far with anonymization, you can easily strip out the critical details that researchers and analysts need. It’s a classic case of throwing the baby out with the bathwater.
Imagine a medical study where you lump all patient ages into a broad "40-60" category. While that certainly protects individual identities, it makes the data completely useless for a researcher trying to understand how a disease progresses differently for someone who is 42 versus someone who is 58. The real art is finding that sweet spot where the data is safe, but the story it tells is still clear.
This fundamental tension between security and utility is something you'll constantly grapple with. Every single technique, whether it's removing data or slightly altering it, comes with a trade-off. To choose the right approach, you need to understand not just the mechanics of anonymization, but also exactly what you hope to learn from the data itself.
The Ever-Present Risk of Re-Identification
One of the sneakiest and most persistent threats is the linkage attack. This is where a determined individual takes your supposedly "anonymous" dataset and combines it with other public information to put the pieces back together and re-identify people.
Even after you've diligently removed obvious identifiers like names and social security numbers, other bits of data can act as a unique fingerprint.
For instance, a dataset might contain just three pieces of information: a person's 5-digit zip code, their full birth date, and their gender. On their own, these seem pretty generic. But research has famously shown that this simple combination is unique for a shocking 87% of the U.S. population. If an attacker gets a public voter roll, they can cross-reference it with your "anonymous" data and, just like that, connect the dots back to a specific person.
This is precisely why true anonymization has to be more sophisticated than just deleting a few columns. It’s about thinking like an attacker and anticipating how seemingly harmless data points could be reassembled.
The Hurdles of Scale and Messy Data
Today’s massive datasets bring their own set of problems. Running sophisticated anonymization algorithms across terabytes—or even petabytes—of information requires a tremendous amount of computational power. For organizations that need to process data in real-time, the processing delays and associated costs can be a major roadblock.
On top of that, a lot of valuable data doesn't come in neat, organized spreadsheets. We're often dealing with a huge amount of unstructured, messy data, such as:
- Clinical notes: A doctor's free-form text about a patient visit can be packed with names, family details, and specific locations.
- Medical images: The metadata embedded in DICOM files often contains a treasure trove of patient information right in the headers.
- Audio recordings: Voice notes from patient consultations can contain identifiable voices and deeply personal stories.
Scrubbing this kind of information is a whole different ballgame compared to cleaning a simple database. It often requires specialized tools like Natural Language Processing (NLP) to intelligently find and redact sensitive text, or specific software designed to parse and clean image metadata. Handling this complexity means you need a much more advanced strategy to ensure no private information gets left behind.
Here's a human-written version of the section, following all your requirements:
How to Build a Real-World Data Anonymization Strategy
Putting together a solid data anonymization plan isn’t a one-and-done task. It's more like a commitment—a continuous effort to balance legal requirements, the need for good data, and the ever-present security risks. A great strategy is one that's built to last, woven right into the fabric of how your organization handles data.
The journey always begins with a detailed risk assessment. You can't protect what you don't know you have. The first step is to pinpoint exactly where all your sensitive data is stored and then categorize it based on how easily it could be traced back to an individual. This map becomes your guide for everything that follows.
The Building Blocks of a Strong Framework
With a clear picture of your data landscape, you can start building the practical parts of your strategy. This is where you pick your tools and set the ground rules for your team.
A reliable plan always includes these core components:
- Choosing the Right Tools for the Job: Select anonymization techniques that fit what you need to do with the data. If you’re setting up a realistic test environment, data masking is a fantastic choice. But for large-scale research where you're looking at broad trends, a technique like perturbation might be a better fit.
- Creating Clear Policies: You need a formal data governance policy that leaves no room for ambiguity. This document should spell out who's in charge of anonymizing data, who gets to access it, and the specific conditions for that access.
- Integrating and Automating the Process: Anonymization shouldn't be an afterthought. Build it directly into your existing data pipelines. Automating the process wherever you can is a huge win—it ensures consistency and dramatically cuts down on human error, which is especially critical when you’re dealing with a constant flow of new information.
Anonymization Isn't a Project; It's a Process
The world of data privacy doesn't stand still. New ways to re-identify people from anonymous data pop up all the time, which means your strategy can't afford to get stale. Truly effective anonymization requires constant attention and a willingness to adapt.
Anonymization is not a "set it and forget it" solution. It’s a living cycle of implementation, testing, and making improvements. The real goal is to stay ahead of the curve by treating privacy as the dynamic challenge it is.
Make it a habit to test your anonymized datasets. Try to break them. See if you can link the data back to individuals using other public information. Run regular audits to make sure everyone is following the rules and that your methods are still holding up. By creating this feedback loop, you build a privacy program that not only protects your data today but is also ready for whatever comes next.
Your Data Anonymization Questions, Answered

As you dive into the world of data anonymization, some questions pop up time and time again. Let’s clear up a few of the most common ones.
What's the Difference Between Anonymization and Encryption?
Think of it this way: anonymization is like redacting a document permanently, while encryption is like locking it in a safe. Anonymization aims to strip out personal identifiers for good so the data can be used for analysis without revealing who it’s about. The goal is to make it irreversible.
Encryption, on the other hand, is all about reversibility. It scrambles data into an unreadable format that can only be unlocked with the right key. This is perfect for protecting data while it's being stored or sent, ensuring only the people with the key can see the original, sensitive information.
Can Anonymized Data Ever Be Traced Back to an Individual?
Unfortunately, yes. While the goal is to make re-identification impossible, there’s always a small risk if the anonymization wasn’t done well enough. Someone could potentially cross-reference the anonymized dataset with other publicly available information to connect the dots. This is often called a linkage attack.
This is precisely why the how of anonymization matters so much. A skilled analyst with enough external data could piece together seemingly innocent information to uncover a person's identity, which underscores the need for robust methods and constant diligence.
Does All Data Need to Be Anonymized?
Not at all. Anonymization is specifically for data that can identify a person—what regulations like GDPR call personal data or what we often refer to as personally identifiable information (PII).
If the information can't be used to single someone out, it doesn't need this treatment. Think about data like broad sales trends, anonymous website traffic statistics, or readings from industrial equipment. The first critical step is always figuring out which pieces of your data could actually point to a real person.